The problem: I need to measure how much power different Android applications make the phone to consume.
Measurement method: Measure how much current the phone takes from it’s own battery. So I needed to somehow attack a measurement device between battery terminal and battery contact on the phone. This could be made by using a piece of dual side flexible circuit board put between the contacts. It would allow to pass the current through any suitable current measurement device. I did not have suitable flexible circuit board material around, so I used few pieces of Kapton tape and copper tape to make a good replacement for it. Two copper tapes and a layer of Kapton tape between them as insulation is the construction I used. It is flexible and could be easily cut to needed shape. And I can easily solder the connector to it (copper is easy to solder and Kapton is heat resistant).
Then I just had to put it to battery over plus terminal and feed the signals from free end to multimeter current input.
Because in this project I would be dealing with lithium batteries (that are potentially dangerous when short circuited) and somewhat expensive hardware (smart phone), I had to be careful what to do. I did first proof-of-concept with old Nokia N73 phone, and when I I could work with it, I moved to the planned target: Samsung Galaxy Trend+. I selected a decent cheaper end Android phone (around 100-120 Euros) as test subject because if something goes wrong I loose much less money than with top-of-the line phones (400-700 Euros).
When the the measurement had was carefully put to right place on battery and secured to it, and everything that could make short circuit outside measurement are were insulated with kapton tape, I could safely put the battery to phone. I do not want to cause any potentially disasters with any unwanted short circuits.
I wired the signal to UT-81B multimeter/oscilloscope. First I used the current measurement range provided by UT-81B. With it I could easily get idea of the current that goes. I could easily see the current changing from few mA to around 500 mA depending on what is done with the phone. If I connect the USB charger, I get 300-400 mA on the other direction. Things work well here, but on the oscilloscope screen I could easily see that the current changes a lot at quick pace, typically there are short quite high spikes and then times with less current. If I measure the current with multimeter current range, and log the results once per second to PC, there is risk of serious measurement errors on average current.
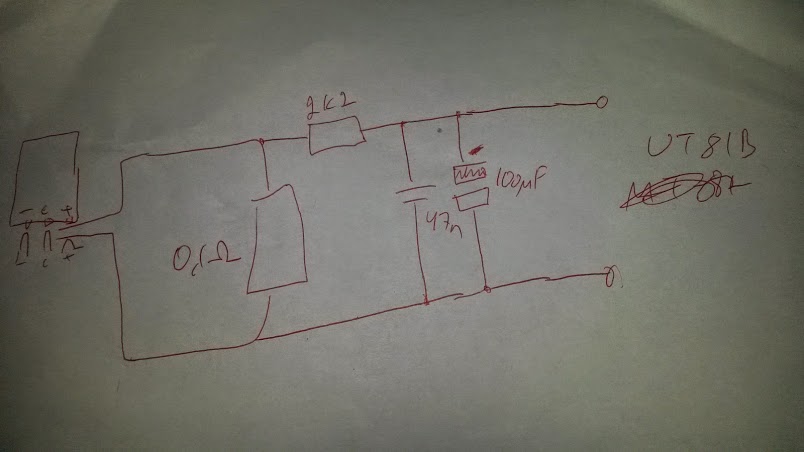
I needed something more clever, something that can filter me the average current reading that I can log. I came up with the following circuit that consists of 0.1 on resistor shunt followed with a low pass filter (around 2 seconds time constant). The low pass filter will integrate me a voltage comparable to average current, and it does not change too quickly for logging once per second.
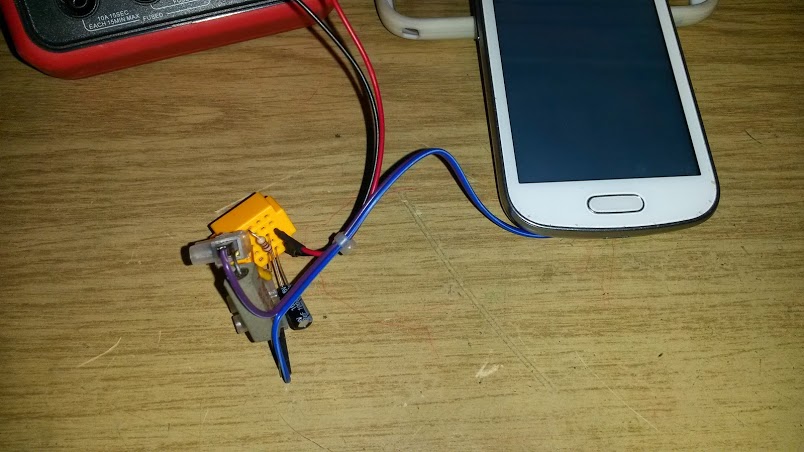
I built the circuit to small breadboard. The current carrying wires are directly screwed to the resistor wires instead of going though the breadboard (four terminal sensing style apprach) to minimize the effect of contact resistance near 0.1 ohm resistor (the resistance is so small that even small contact resistances can cause considerable measurement error).
The circuit output is so that I get 1 mV out per every 10 mA. With UT-81B multimeter DC measurement resolution of 100 uA, I could get resolution down to 1 mA. This is well workable solution. Now I just had to connect the multimeter with optically isolated USB connection to PC and use UT-81B software to log the data from multimeter. The software can easily log time-stamped data in every 1-2 seconds and save them in a format that could be opened with Excel. I have now a good test setup. I could measure the current consumption at 1 mA resolution and at round 5% accuracy (I compared DC reading with another multimeter). With a little bit calibration the circuit could be made even more accurate.





8 Comments
Tomi Engdahl says:
Links to some related videos:
Galaxy Nexus Screen power consumption
http://www.youtube.com/watch?v=cqSQ5QE-4S0
Samsung Galaxy S3 Power Consumption Test.
http://www.youtube.com/watch?v=KD8HzaruWAU
Tomi Engdahl says:
Some more reading:
The Systems Hacker’s Guide to the Galaxy
Energy Usage in a Modern Smartphone
http://www.nicta.com.au/pub?doc=7044
Instrumentation
Modern consumer devices such as smartphones have
a large number of power supplies for various compo-
nents, which, in theory, enable per-component analysis
of power consumptions. However, there are generally no
schematics available which would help identify the sup-
plies powering each component, nor are they equipped
with measurement capability.
Display power is a significant contributor in every sce-
nario where the display is active. Even at the 50% bright-
ness level it contributes 300–600 mW, highly dependent
on the image content—an inherent property of OLED
technology.
Tomi Engdahl says:
How to Determine What is Using Battery Power on a Galaxy Tab
http://www.dummies.com/how-to/content/how-to-determine-what-is-using-battery-power-on-a-.html
he Samsung Galaxy Tab is smart enough to know which of its features use the most battery power. You can check it out for yourself:
At the Home screen, touch the Apps Menu icon button.
Choose Settings.
Choose About Tablet.
Choose Battery Use.
The number and variety of items listed on the Battery Use screen depend on what you’ve been doing between charges and how many apps you’re using.
Tomi Engdahl says:
Energy Consumption in Android Phones when using Wireless Communication Technologies
https://bib.irb.hr/datoteka/575153.Energy_Consumption_in_Android_Phones_when_using_Wireless_Communication_Technologies.pdf
Tomi Engdahl says:
Galaxy Nexus Power Analysis: Why chargers can’t keep up with navigation. (Plus, black screens draw less power than white… sometimes!)
http://www.reddit.com/r/Android/comments/nystt/galaxy_nexus_power_analysis_why_chargers_cant/
Tomi Engdahl says:
Apps help identify mobile code ‘energy hotspots’
http://www.edn.com/electronics-products/other/4436438/Apps-help-identify-mobile-code–energy-hotspots-?_mc=NL_EDN_EDT_EDN_weekly_20141030&cid=NL_EDN_EDT_EDN_weekly_20141030&elq=192325cf30f142a49b18623d0e0021d4&elqCampaignId=19924
A software startup company based on a Purdue University innovation is helping to extend the life of smartphone batteries by helping application developers identify code that drains batteries quickly.
“There are two ways to address the problem of smartphone batteries draining quickly: the first is to invent a better battery. Battery capacity, which is the amount of energy that can be packed into a fixed form factor, is reaching its limit,” said Hu. “The other option is to make smartphone apps more energy efficient so they drain less of the battery. Mobile Enerlytics is developing software to make that happen.”
Purdue researchers have developed the technology that could help mobile app developers analyze millions of lines of code to identify ‘hotspots,’ or sections of code that drain most of the energy. The technology has been exclusively licensed to Mobile Enerlytics through the Purdue Office of Technology Commercialization.
“As mobile apps become more feature-rich, code easily reaches more than one million lines,” explained Hu. “My colleagues and I have found that a single line of code can create an energy hotspot. Sometimes simply changing the data structure or moving around a single line of code drastically reduces the resulting energy drain.”
“When a smartphone user starts Estar, it provides two options: to find energy-efficient apps in the app market or to stop power-hungry apps running on the phone,” said Hu. “When the first option is chosen, Estar provides a color-coded, five-star rating system that shows how fast a smartphone app will drain the phone battery, in the foreground and in the background, relative to other apps in the same category. Estar also makes a daily recommendation of apps based both on popularity and energy ratings.”
Mobile Enerlytics; http://www.mobileenerlytics.com/
Tomi Engdahl says:
Commercial approach:
BaseMark Announces The Power Assessment Tool (PAT)
by Andrei Frumusanu on March 2, 2016 10:01 AM EST
http://www.anandtech.com/show/10111/basemark-announces-the-power-assessement-tool
Basemark has traditionally been a software company. We’ve seen and used a lot of their benchmarking test suites including Basemark OS and Basemark X. Seeking to expand its portfolio by not only providing software benchmarks to quantify performance of devices, Basemark looks to provide hardware to enable users to measure power-consumption and power-efficiency of devices. Here is where the PAT (Power Assessment Tool) comes in. The PAT is a tool that doesn’t require destructive dismantlement of a device to be able to measure its power consumption. This is an area where I’m particularly familiar with as over the last year and more have been instrumenting a lot of smartphones via external power supplies and measurement equipment by physically opening them and replacing the lithium power cells.
Basemark relies on the fact that when smartphones are fully charged, they usually enter a power bypass-mode where the internal battery cell is no longer used, and power is instead drawn directly from the connected charger. To do this the PAT is connected to a conventional charger input. Currently this is a microUSB port but Basemark tells me future revisions might consider going USB C.
It’s still a bit early to talk about the capabilities of the beta software but Basemark shows promise and once all features are implemented the PAT should represent great value in terms of analysis for both professionals and enthusiastic hobbyists.
Tomi Engdahl says:
A volt out of the blue: Phone batteries reveal what you typed and read
Power trace sniffing, a badly-designed API and some cloudy AI spell potential trouble
https://www.theregister.co.uk/2018/06/25/the_battery_is_the_smartphones_ibesti_snitch_boffins/
A group of researchers has demonstrated that smartphone batteries can offer a side-channel attack vector by revealing what users do with their devices through analysis of power consumption.
Both snitching and exfiltration were described in this paper (PDF), accepted for July’s Privacy Enhancing Technologies Symposium.
Nobody needs to panic yet, because the attack isn’t yet more than a decently tested theory,
https://sites.google.com/site/silbersteinmark/Home/popets18power.pdf?attredirects=1