The RSA SecurID authentication mechanism consists of a “token” — either hardware (e.g. a USB dongle) or software (a soft token) — which is assigned to a computer user and which generates an authentication code at fixed intervals (usually 60 seconds) using a built-in clock and the card’s factory-encoded random key (known as the “seed”). The seed is unique for each token, and is loaded into the corresponding RSA SecurID server (RSA Authentication Manager, formerly ACE/Server) as the tokens are purchased.
I yesterday posted teardown of RSA SecurID 700 token. Here is teardown of the older style RSA SecurID token model SD600.
Here is the bavk of the device some device identification codes hidden.
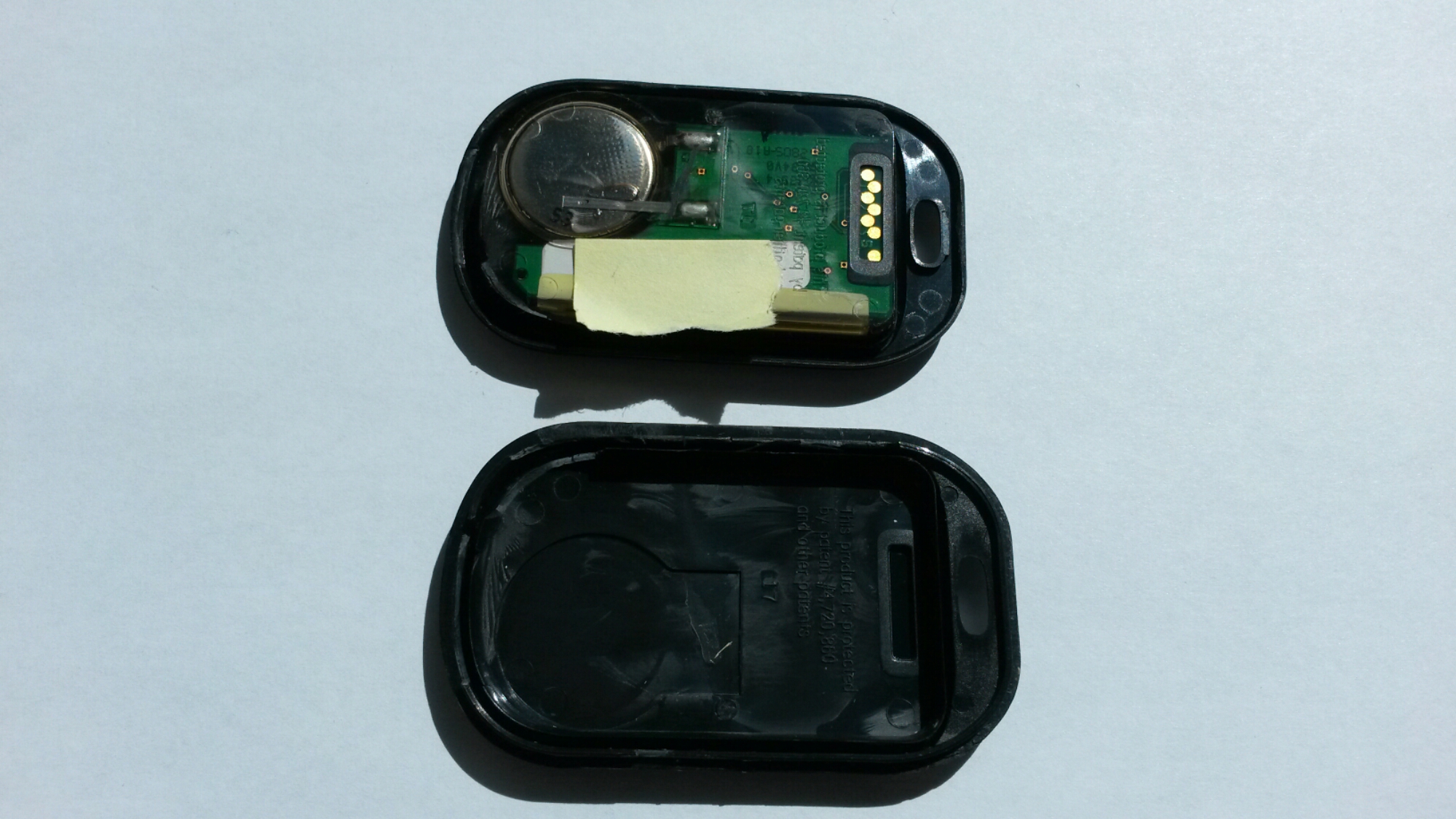
What is inside?
Again all the electronics was cast inside some resin that looked a bit hard to remove. So I don’t get to know on which tiny processor thus device runs with. The battery is also inside the same resin (when battery runs out this device is useless waste). Only exposed contacts seem to be those contacts that look like some kind of test/programming connector.
This unit I received still has some battery power left. What tricks could be done with this device? Anyways I have understood that those old SecurID devices are not very secure anymore.
A little bit searching on the Internet reveals other teardowns that dig deeper into the secrets of the device. RSA SecureID Teardown article has this nice picture of the circuit board components:
Under the hood: SecurID fob: single-chip safety net article has also some more details. on this device.





0 Comments
Be the first to post a comment.