Some critical systems aren’t exposed to the public internet and sit, apparently safely, in an isolated environment, air gapped from the rest of the world by a lack of internet connectivity. The integrity of the air gap is only maintained when the means of data transport in and out of the environment are equally subject to the highest levels of security. In practice, the integrity of air gapped networks has proven to be extremely difficult to maintain. Here are some new techniques how air gapped system can leak sensitive data:
ETHERLED: Air-gapped systems leak data via network card LEDs
https://www.bleepingcomputer.com/news/security/etherled-air-gapped-systems-leak-data-via-network-card-leds/
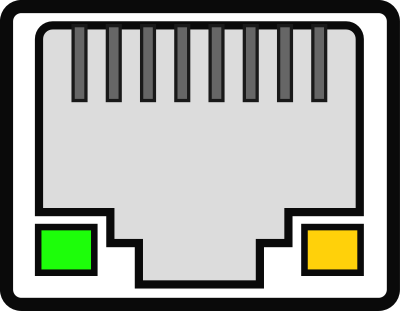
Israeli researcher Mordechai Guri has discovered a new method to exfiltrate data from air-gapped systems using the LED indicators on network cards. Dubbed ‘ETHERLED’, the method turns the blinking lights into Morse code signals that can be decoded by an attacker. Capturing the signals requires a camera with a direct line of sight to LED lights on the air-gapped computer’s card.
The attack begins with planting on the target computer malware that contains a modified version of the firmware and/or driver for the network card. This allows taking control of the LED blinking frequency, duration, and color.
To capture the signals remotely, threat actors can use anything from smartphone cameras (up to 30 meters), drones (up to 50m), hacked webcams (10m), hacked surveillance cameras (30m), and telescopes or cameras with telephoto or superzoom lenses (over 100 meters).
New Air Gap-Jumping Attack Uses Ultrasonic Tones and Smartphone Gyroscope
https://www.securityweek.com/new-air-gap-jumping-attack-uses-ultrasonic-tones-and-smartphone-gyroscope
A researcher from the Ben-Gurion University of the Negev in Israel has shown how a threat actor could stealthily exfiltrate data from air-gapped computers using ultrasonic tones and smartphone gyroscopes. The attack method, named GAIROSCOPE, assumes that the attacker has somehow managed to plant malware on the air-gapped computer from which they want to steal data, as well as on a smartphone that is likely to go near the isolated device.
The air-gapped computer can transmit ultrasonic tones using the device’s loudspeakers. These tones are inaudible and on a frequency that is picked up by a gyroscope. On the phone side of the attack, the infected device’s gyroscope picks up those tones when it’s near the air-gapped computer.
GAIROSCOPE: Injecting Data from Air-Gapped
Computers to Nearby Gyroscopes
https://arxiv.org/pdf/2208.09764.pdf
4 Comments
Tomi Engdahl says:
https://www.securityweek.com/new-air-gap-jumping-attack-uses-ultrasonic-tones-and-smartphone-gyroscope
Tomi Engdahl says:
https://techcrunch.com/2022/08/24/gairoscope-air-gap-attack/
Tomi Engdahl says:
https://www.bleepingcomputer.com/news/security/etherled-air-gapped-systems-leak-data-via-network-card-leds/
Tomi Engdahl says:
https://nakedsecurity.sophos.com/2022/08/24/breaching-airgap-security-using-your-phones-compass-as-a-microphone/