Nothing is perfect. The most common digital security technique used to protect both media copyright and Internet communications has a major weakness. RSA authentication is a popular encryption method. he RSA algorithm gives security under the assumption that as long as the private key is private, you can’t break in unless you guess it. Researchers find weakness in common digital security system tells that University of Michigan computer scientists have found they could foil the security system by varying the voltage supply to the holder of the “private key”.
They carefully manipulated the operating voltage of the computer electronics (FPGA). This causes it to make small mistakes in its communications with other clients (if it would make big mistakes it would crash). These faults reveal small pieces of the private key, and enough faults allows the researchers reconstruct the key offline. It takes considerable amount of time (100 hours) and many servers (
For more details read the whole FaultBased Attack of RSA Authentication paper. It describes an end-to-end attack to a RSA authentication scheme on a complete FPGA-based SPARC computer system and demonstrates that a fault-based attack on the RSA algorithm is possible.
It is highly unlikely that a hacker could use this approach on a large institution, so the risk of this to you could be pretty low. The researches say that a common cryptographic technique called “salting” that changes the order of the digits in a random way every time the key is requested, can help to fix this problem. There could also be other solutions as well (maybe better hardware more immune to error).
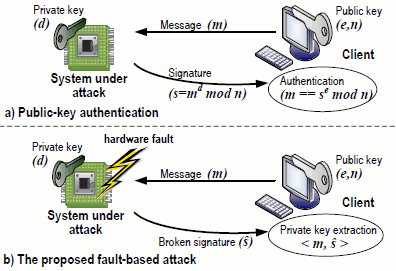
Image source: http://www.eecs.umich.edu/~valeria/research/publications/DATE10RSA.pdf
1 Comment
Teknik Informatika says:
How does the fault-based attack on RSA authentication, as demonstrated by University of Michigan computer scientists, exploit variations in voltage supply to compromise the private key, and what are the implications of such vulnerabilities for digital security systems relying on RSA encryption? Regards Telkom University