It is scary how many industries (e.g. autos, “smart” electronics, control systems) are decades behind state of the art security. It’s Easy To Hack Traffic Lights Slashdot posting tells about article where research from the University of Michigan are into the ease with which attackers can hack traffic lights. The network is IP-based, with all the nodes (intersections and management computers) on a single subnet. The 5.8GHz network has no password and uses no encryption; with a proper radio in hand, joining is trivial.
The researcher team has written a paper Green Lights Forever: Analyzing the Security of Traffic Infrastructure, an adversary can control traffic infrastructure to cause disruption, degrade safety, or gain an unfair advantage. The paper gives details on the security flaws that exist due to systemic failures by the designers, gives recommendations on how to improve existing systems and discuss the lessons learned for embedded systems security in general. This is good reading for anybody who is interested in the security of modern infrastructure (let it be smart city or industrial site).
2 Comments
Tomi Engdahl says:
Green Light Your Commute with America’s Unsecured Traffic Lights
http://hackaday.com/2014/08/31/green-light-your-way-to-an-easy-commute/
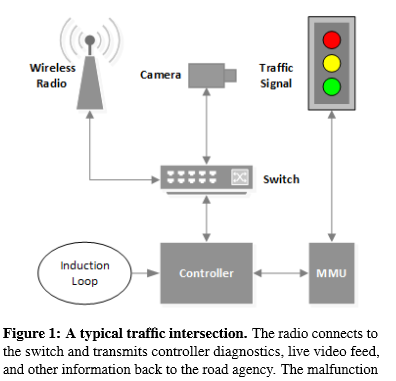
The study points out that a large portion of traffic lights in the United States communicate with each other wirelessly over the 900Mhz and 5.8Ghz ISM band with absolutely no encryption. In order to connect to the 5.8Ghz traffic signals, you simply need the SSID (which is set to broadcast) and the proper protocol. In the study the researchers used a wireless card that is not available to the public, but they do point out that with a bit of social engineering you could probably get one.
Another route is the HackRF SDR, which could be used to both sniff and transmit the required protocol. Once connected to the network you will need the default username and password, which can be found on the traffic light manufacturer’s website.
To gain access to the 900Mhz networks you need all of the above and a 16-bit slave ID.
Once on the network you have two options. The completely open debug port in the VxWorks OS which allows you to read-modify-write any memory register. Or by sending a(n) UDP packet where the last byte encodes the button pressed on the controller’s keypad. Using the remote keypad you can freeze the current intersection state, modify the signal timing, or change the state of any light. However the hardware Malfunction Management Unit (MMU) will still detect any illegal states
Tomi Engdahl says:
Australian traffic lights need better security says auditor-general
Poor passwords, proprietary code … what could possibly go – CRASH! – wrong?
http://www.theregister.co.uk/2015/01/22/nsw_traffic_lights_need_better_infosec_auditorgeneral/
The Auditor-General of the Australian State of New South Wales (NSW) and the state’s roads bureaucrats are at loggerheads over whether or not traffic signal infrastructure is vulnerable to attacks over the Internet.
In a report on critical infrastructure security, the audit office asserts that “systems in place to manage traffic signals are not as secure as they should be”.
The report adds that “there is a potential for unauthorised access to sensitive information and systems that could result in traffic disruptions, and even accidents in one particular section of the road network”.
The report, naturally enough, doesn’t identify where the vulnerabilities might exist.
The bloodstream of the network is the locally-developed SCATS – Sydney Co-ordinated Adaptive Traffic System – which was first developed in the 1970s by the current Roads & Maritime Services predecessor, the Roads and Traffic Authority.
The auditor identifies key risks as being poor SCATS password control; and asserts that some servers in the network are only receiving anti-virus updates on a weekly basis
There’s also concern that the roadside cabinets – the immediate control of traffic signals – are too easy to break into, that staff aren’t well trained to respond to security incidents, and that some software isn’t patched frequently enough.
TfNSW, however, isn’t certain that things are dire. In its response, published as part of the report, it states:
“Whilst Transport accepts that there is a possibility for unauthorised access to sensitive information and systems, as there is for all inter-connected industrial control systems, we refute the suggestion the result could ” … cause accidents on one particular section of the road network”.”
Even the auditor’s report notes that attacks on the traffic light infrastructure are unlikely to lead to a cascade of Camrys nose-to-tailing:
“Traffic light controllers are highly resistant to standard hacking techniques. The devices in use have been certified to formal Australian Standards that require safety interlocks. These interlocks are used to prevent simultaneous green lights creating a dangerous situation at an intersection.”
The same report also recommended improvements to the Sydney Water security infrastructure
Security of Critical IT Infrastructure
http://www.audit.nsw.gov.au/publications/performance-audit-reports/2015-reports/security-of-critical-it-infrastructure/security-of-critical-it-infrastructure