There is a serious problem in new TCP feature designed to prevent hacking: it makes possible to make easily man-in-the-middle type attacks from anywhere. Feature is built into Linux kernel 3.6-4.7 (patch on newest version available).
https://www.rt.com/usa/355558-linux-vulnerability-websites-attacks/
At the symposium, the researchers demonstrated the exploit by injecting code into a live USA Today page that asks visitors to enter their emails and passwords, which was possible because pages on USA Today aren’t encrypted.
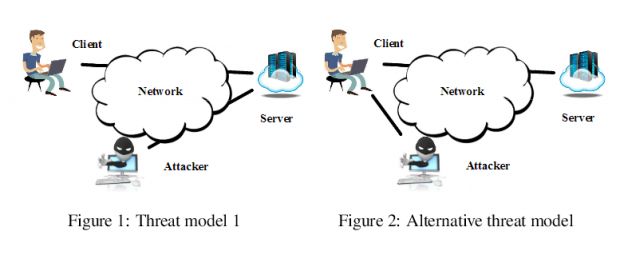
Perhaps most importantly, the intercepting of data doesn’t require a man-in-the-middle attack, where a connection will covertly intercept, collect and pass forward information between two parties. Instead, attackers can just send packets of data to the two targets with spoofed credentials.
“Through extensive experimentation, we demonstrate that the attack is extremely effective and reliable. Given any two arbitrary hosts, it takes only 10 seconds to successfully infer whether they are communicating,”
Because Linux runs in the backend on a majority of servers as well as on Android devices, an enormous number of users might be left vulnerable. Even those using the much-vaunted anonymizing software Tor could have their privacy compromised 90 percent of the time in an average time of about 50 seconds.
The team notes that because only version 3.6 or later of the Linux kernel has the flaw, systems running older software are not affected.
CVE-2016-5696 is the ID of a serious security flaw that affects the TCP implementation in the Linux kernel, which, if exploited, allows an attacker to hijack unencrypted Web traffic, or crash encrypted communications such as HTTPS sessions or Tor connections.
The vulnerability affects all Linux kernel versions between v3.6 and up to v4.7 and existed in the Linux kernel for the past four years. At the heart of the problem is the design of the RFC 5961, a standard that dictates how TCP connections are established between two hosts.
CVE-2016-5696 can also be used to create a Denial of Service (DoS) state for encrypted services such as SSH and Tor.
The paper titled Off-Path TCP Exploits: Global Rate Limit Considered Dangerous presents a case study where the six researchers injected a phishing form inside the USA Today website.
10 Comments
Tomi Engdahl says:
Research paper can be found at http://www.cs.ucr.edu/~zhiyunq/pub/sec16_TCP_pure_offpath.pdf
Tomi Engdahl says:
USA Today was hijacked by means of TCP bug
American scientists have demo the USENIX Security Conference in Austin, how linux kernel included in a TCP bug can be used to take over the popular website. The demo scientists show how an unencrypted USA Today magazine, the site will be hijacked.
The case of the University of California researchers. They found all Linux operating systems can be found in the vulnerability of the TCP protocol.
The irony is that the opening associated with a relatively new Internet standard, RFC 5691. This is the Linux kernel implemented since 2012.
Source: http://etn.fi/index.php?option=com_content&view=article&id=4818:usa-today-kaapattiin-tcp-bugin-avulla&catid=13&Itemid=101
Tomi Engdahl says:
Pure Off-path TCP attack demo by using a side channel in Recent Linux Kernel
https://www.youtube.com/watch?v=S4Ns5wla9DY
See more details in our paper “Off-Path TCP Exploits: Global Rate Limit Considered Dangerous”. This vulnerability is filed as CVE-2016-5696
http://www.cs.ucr.edu/~zhiyunq/pub/sec16_TCP_pure_offpath.pdf
Tomi Engdahl says:
It seems that Android devices could be safe from this if the following is correct:
http://android.stackexchange.com/questions/51651/which-android-runs-which-linux-kernel
Table from Wikipedia:
Android Version |API Level |Linux Kernel in AOSP
—————————————————-
1.5 Cupcake |3 |2.6.27
1.6 Donut |4 |2.6.29
2.0/1 Eclair |5-7 |2.6.29
2.2.x Froyo |8 |2.6.32
2.3.x Gingerbread |9, 10 |2.6.35
3.x.x Honeycomb |11-13 |2.6.36
4.0.x Ice Cream San|14, 15 |3.0.1
4.1.x Jelly Bean |16 |3.0.31
4.2.x Jelly Bean |17 |3.4.0
4.3 Jelly Bean |18 |3.4.39
4.4 Kit Kat |19, 20 |3.10
5.x Lollipop |21, 22 |3.16.1
6.0 Marshmallow |23 |3.18.10
Note: other “distributions” of Android might run different kernel versions.
https://en.wikipedia.org/wiki/Android_version_history
Tomi Engdahl says:
https://www.quora.com/Why-is-Android-stuck-on-Linux-3-4
Why is Android stuck on Linux 3.4?
Since its inception, Android has followed the Linux kernel pretty closely. Sure it was always a few releases behind, but basically every version of Android got a new Linux kernel. However since JellyBean 4.2, Android has been stuck on Linux 3.4. Does anyone have an anwer for this?
I believe that Android Phone’s kernel version largely depends on OEM’s feature requirements and their ability to patch the mainline kernel to make it compatible with their device.
Tomi Engdahl says:
The weakness of TCP protocol implementation for Linux
vulnerability found in TCP protocol Linux implementation allows for the interception of TCP connections, data connections and disconnection for sneaking.
The vulnerability is based on the RFC5961: first presented at Challenge ACK -vastauspakettien as well as their responses to limit the transmission rate of the global rate limit implementations of the exploitation.
Vulnerable servers are Linux, with kernel version is 3.6 or later. Linux kernel 3.6 was published in 2012.
According to FICORA, the attack method can be utilized in practice only in long-term TCP connections. the case of encrypted connections vulnerability can only be used to cut the connections. Long-term non-encrypted connections are used, for example, automatically updating web pages such as news sites, IRC connections, downloads or video services.
Attack method can be utilized in practice only in long-term TCP connections. the case of encrypted connections vulnerability can only be used to cut the connections. Long-term non-encrypted connections are used, for example, automatically updating web pages such as news sites, IRC connections, downloads or video services.
So far, the vulnerability has not been offered compensation, but its use may be limited by changing the linux kernel parameter tcp_challenge_ack_limit.
Sources:
http://www.tivi.fi/Kaikki_uutiset/linux-ytimesta-loytyi-vuosia-vanha-paha-haavoittuvuus-korjausta-ei-ole-olemassa-6573289
https://www.viestintavirasto.fi/kyberturvallisuus/haavoittuvuudet/2016/haavoittuvuus-2016-107.html
Tomi Engdahl says:
Linux bug leaves 1.4 billion Android users vulnerable to hijacking attacks
Off-path attack means malicious hackers can be located anywhere on the Internet.
http://arstechnica.com/security/2016/08/linux-bug-leaves-1-4-billion-android-users-vulnerable-to-hijacking-attacks/
An estimated 80 percent of Android phones contain a recently discovered vulnerability that allows attackers to terminate connections and, if the connections aren’t encrypted, inject malicious code or content into the parties’ communications, researchers from mobile security firm Lookout said Monday.
As Ars reported last Wednesday, the flaw first appeared in version 3.6 of the Linux operating system kernel, which was introduced in 2012. In a blog post published Monday, Lookout researchers said that the Linux flaw appears to have been introduced into Android version 4.4 (aka KitKat) and remains present in all future versions, including the latest developer preview of Android Nougat. That tally is based on the Android install base as reported by statistics provider Statista, and it would mean that about 1.4 billion Android devices, or about 80 percent of users, are vulnerable.
“The tl;dr is for Android users to ensure they are encrypting their communications by using VPNs, [or] ensuring the sites they go to are encrypted,” Lookout researcher Andrew Blaich told Ars. “If there’s somewhere they’re going to that they don’t want tracked, always ensure they’re encrypted.”
The vulnerability makes it possible for anyone with an Internet connection to determine whether any two parties are communicating over a long-lived transport control protocol connection, such as those that serve Web mail, news feeds, or direct messages. In the event the connections aren’t encrypted, attackers can then inject malicious code or content into the traffic. Even when the connection is encrypted, the attacker may still be able to determine a channel exists and terminate it. The vulnerability is classified as CVE-2016-5696.
A Google representative said company engineers are are already aware of the vulnerability and are “taking the appropriate actions. As noted in this post, the representative pointed out the flaw resides within vulnerable versions of the Linux kernel and it’s not Android specific. The representative went on to say that the Android security team rates the risk “moderate,” as opposed to “high” or “critical” for many of the vulnerabilities it patches. Maintainers of the Linux kernel have already patched CVE-2016-5696. It wouldn’t be surprising if that fix is incorporated into a new Android release in the next month or so.
Tomi Engdahl says:
Also, the latest Android wounded
Last week it was reported widely on all Linux operating systems looming vulnerability, which also applies to Android mobile phones. Now has been specified, that all the 4.4 version is not after the Kit Kat’s Androids are the vulnerability of the victims. Also, a new Android N, or Nougat.
This is the TCP protocol vulnerability, which has been at the heart of Linux, version 3.6 onwards. The latest at the core of the problem is patched, but it still lurks as much as 1.4 billion Android device. This is about 80 per cent of all available Android devices.
A remote attacker can monitor Internet traffic between two machines, interrupt conversation and fed to communicate something wrong, to their own information.
Source: http://etn.fi/index.php?option=com_content&view=article&id=4847:myos-uusin-android-haavoittunut&catid=13&Itemid=101
Tomi Engdahl says:
Linux Traffic Hijack Flaw Also Affects Most Android Phones, Tablets
https://linux.slashdot.org/story/16/08/15/2038201/linux-traffic-hijack-flaw-also-affects-most-android-phones-tablets
As many as 80 percent of Android devices are vulnerable to a recently disclosed Linux kernel vulnerability. Security firm Lookout said in a blog post on Monday that the flaw affects all phones and tablets that are running Android 4.4 KitKat and later, which comes with the affected Linux kernel 3.6 or newer. According to recent statistics, the number of devices affected might run past 1.4 billion phones and tablets — including devices running the Android Nougat developer preview. Windows and Macs are not affected by the vulnerability
The exploitability isn’t easy, though.
Linux traffic hijack flaw also affects most Android phones, tablets
About 80 percent of all Android devices are affected, but “exploitability is hard.”
http://www.zdnet.com/article/linux-traffic-hijack-flaw-also-affects-most-android-phones-tablets/
The flaw, disclosed at the Usenix security conference last week, is complicated and difficult to exploit. If an attacker can pull off an exploit, they could inject malicious code into unencrypted web traffic from “anywhere”. However, the source and destination IP address would need to be known in order to intercept the traffic, adding to the complexity of carrying out a successful attack.
That might not be so difficult for well-resourced attackers, who are in a privileged position on the network, such as nation states.
Even if the connection is encrypted, an attacker could still determine and terminate a connection — even if they cannot read web traffic. This kind of attack could be used to degrade a privacy and anonymity service, like Tor.
Tomi Engdahl says:
Off-Path TCP Exploits: Global Rate Limit Considered Dangerous
https://www.usenix.org/conference/usenixsecurity16/technical-sessions/presentation/cao
https://www.usenix.org/system/files/conference/usenixsecurity16/sec16_paper_cao.pdf