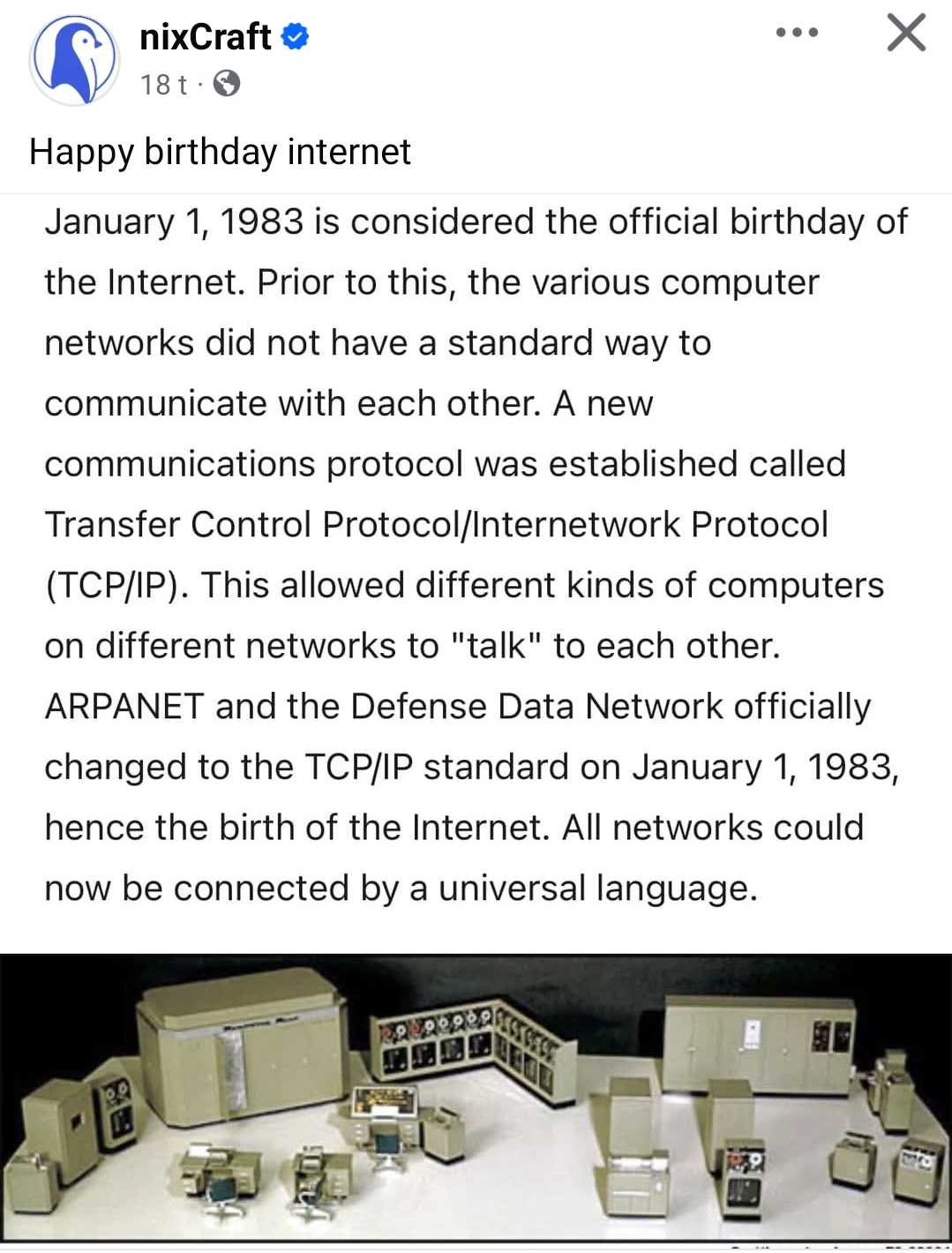
Happy birthday TCP/IP!
We ACKNOWLEDGE you.
Transmission Control Protocol. Internet Protocol.
The deployment of TCP was the birth of the modern Internet — it was the same protocol still in use today. But before TCP, IP networks still had a standard way to communicate: NCP, Network Control Program. It was warty and problematic and limited, but by all accounts it mostly worked.
NCP/IP dates back to 1969, and was unrestricted. TCP just marks the start of the protocol we use today.
The specification;
https://datatracker.ietf.org/doc/html/rfc791?fbclid=IwY2xjawHj5_FleHRuA2FlbQIxMQABHaUUYNRzvN3YgPe4JZW_xulrjuJk6f4ywYU1EvLMJ4lO4fLh40M_Rbw2pA_aem_Dejta7U6dR9J2u5_JV44WQ
7 Comments
that's not my neighbor says:
Happy birthday TCP/IP!
Tomi Engdahl says:
Forgotten Internet: UUCP
https://hackaday.com/2025/01/16/forgotten-internet-uucp/
What’s Forgotten Internet? It is the story of parts of the Internet — or Internet precursors — that you might have forgotten about or maybe you missed out on them. This time, we’re looking at Unix-to-Unix Copy, more commonly called UUCP. Developed in the late 1970s, UUCP was a solution for sending messages between systems that were not always connected together. It could also allow remote users to execute commands. By 1979, it was part of the 7th Edition of Unix.
Operation was simple. Each computer in a UUCP network had a list of neighbor systems. Don’t forget, they weren’t connected, so instead of an IP address, each system had the other’s phone number to connect to a dial up modem. You also needed a login name and password. Almost certainly, by the way, those modems operated at 300 baud or less.
If a computer could dial out, when someone wanted to send something or do a remote execution, the UUCP system would call a neighboring computer. However, some systems couldn’t dial out, so it was also possible for a neighbor to call in and poll to see if there was anything you needed to do. Files would go from one system to another using a variety of protocols.
While UUCP was the name of the system (and UUCPNET the network of all computers reachable by UUCP), there were actually a few programs only one of which was named uucp. That program was the user’s interface to the system.
Other programs included uux for remote command execution, uucico which was the backend, and uustat which provided status information. Every hear of uuencode and uudecode? Those started here and were meant to convert binary to text and vice-versa, since you couldn’t be sure all the modems and computers could handle 8-bit data.
When uucico answers a call, it sends a Control+P along with a string indicating its host name. The caller responds with its own Control+P and host name, along with some options. If the caller isn’t recognized, the computer will hang up.
File Transfer
If the call continues, the caller can either send a file, request a file, send commands to execute, or ask for a hangup. Sending and receiving files or commands use g-protocol. Each packet was a Control+P, a number indicating packet size or type, a 16-bit checksum, the datatype, and a check digit for the header (the checksum didn’t cover the header).
Reading the Mail
An important use of UUCP was early e-mail. Mail programs would cooperate with UUCP. UUCP E-mail addresses contain exclamation points (bangs) to identify the whole path to your machine. So, if you lived in New York and wanted to send an e-mail to Hackaday in California, it might require this address: NY4!east.node!center!west.node!CA8!Hackaday!alwilliams.
It was common, then, to provide your e-mail address relative to some “well-known” node like “…!west.node!CA8!Hackaday!alwilliams.” It was up to the sender to fill in the first part. Your mail would travel through each computer. There could easily be more than one path to …!Hackaday!alwilliams even from the same starting point and there would almost certainly be different paths from different starting hosts.
Usenet was also distributed this same way. Usenet deserves its own Forgotten Internet installment, but it was an early form of what we think of today as discussion groups.
Keep in mind that in both cases, UUCP didn’t know anything about machines more than one hop away. It was up to the mail program to understand that it was running on west.node and that it should then dial up the CA8 computer and transmit the message to it.
IT Telkom says:
Despite its limitations, how did NCP manage to function in the early stages of IP networks? Universitas Telkom
Tomi Engdahl says:
Forgotten Internet: Giving (or Getting) The Finger
https://hackaday.com/2025/01/30/forgotten-internet-giving-or-getting-the-finger/
Based on RFC 742, Finger was the brainchild for [Les Earnest]. From a user’s point of view, you put a few files in your home directory (usually .project and .plan; both hidden files), and when someone “fingered” you, they’d see some human-friendly output about your account like your name and office location, if you were logged in or not, and the contents of your project and plan files.
Modern versions may also show your public PGP key and other data. You could usually put a file in your home directory called .nofinger if you wanted to stop people from fingering you.
Behind the scenes, finger worked with a daemon on port 79 that handled TCP requests. By 1991, RFC 1288 defined the protocol in more detail. Since it was a network service, you could finger people on other computers as long as port 79 was open.
Finger is from a simpler time when you could assume people weren’t trying to hack into your system. Of course, they are. In 1988, the Morris worm exploited fingerd — the finger daemon — to spread itself among systems.
Between better alternatives, security concerns, and a general lack of awareness among new users, the writing was on the wall. Today, it is hard to find a system that provides finger services.
You could install finger, but we don’t recommend you keep it running for long. Ubuntu’s package manager, at least, will let you install both finger and fingerd easily.
In the 1980s, it seemed like finger would be around forever. But network tech can go from ubiquitous to forgotten in a flash. Just like UUCP in our last installment.
Tomi Engdahl says:
TCP/IP is not a TheyCanPingIT Protocol, it is a meal
Tacos Chips Pasta / Includes Pop
Tacos de Carne Picada / includes pico
Tacos, Cupcakes, and Pickles / Intergalactic Penguins
Tomi Engdahl says:
Transmission by Carrier Pigeon
Two Cans Pabst / I Pee
The chick pees / I pee
This Confuses People / I Pass.
Tango Charlie Papa / India Papa
Technically corrupted people / Innocent people
The Computer Pauses / I’m Praying
Too Many Clowns In Public
To Connect People / Idiot People
Too Many Clowns In Public
Thought Control Program / Intelligence Prohibited
Trump Control Port
Total Chaos Protocol / Infinite Packets
Total Control Prompt / Indifferent Personality
Technical Computer Pairing/Interface Pairing.
The Computer Peed Its Pants
Too many CEO Positions are not Idiot Proof
To cause problems/ insolvable problems
The Coolest Printer Is Practical.
Traction Control parameters – infinitely problematic.
Too much coffee protocol: I pee
Trump Control Port/ In Pence
Two Cream Pies/In Pants
The Cheese Protocol / Includes Parmesan
Too cool people/Introverted People
Totally Cool Parties / Insignificant Parties
“The clown posse is petrified “ – Eminem
Sprunki Game says:
Happy birthday to the protocol that keeps the Internet talking!